
ssh is a vital tool in the programmer's arsenal. Enabling the ability to login to servers remotely via the terminal. While this is the main functionality of ssh, there is plenty of things it offers that can improve your usage and understanding of ssh. I won't be covering; creating your own identity via ssh keys, ssh-copy-id, using ssh with git, or the fact that sftp, scp and rsync use ssh. But if you think I should, do reach out to me.
Note: Information in this article is about OpenSSH, which is the main binary and standard of the ssh util.
1. Don't remember, use ~/.ssh/config
ssh allows you to set configurations for remote hosts, this config file lives in .ssh
within your home directory. You can also make a global configuration at /etc/ssh/ssh_config for all users on your system
but usually, this isn't desired. A simple use-case for this is adding friendly names to your servers.
So stop remembering IP addresses and Hostnames, just alias them.
# ~/.ssh/config
Host myserver
Hostname 192.168.1.10
User admin
Host myotherserver
Hostname 192.168.1.23
User administratorThis enables me to do ssh myserver or ssh myotherserver, rather than ssh [email protected] or ssh [email protected] respectively.
This is the most basic usage of the config file, but it offers way more than just this. A full list can be
found here, I will be covering a few more within the following headings.
1a. Separate your configs
I have multiple config files for personal, organisational and work. I keep them in ~/.ssh/config.d/ and have my main config
file include them all. This allows me to easily seperate them and share them with colleagues without having to remove my personal configs.
# ~/.ssh/config
Include config.d/*
Host * # oh yeah! you can use wildcards in hostnames
Compression yes
# ~/.ssh/config.d/home
Host myserver
Hostname 192.168.1.10
User user
# ~/.ssh/config.d/work
Host webserver
Hostname 192.168.7.23
User admin2. Secure PortForwarding
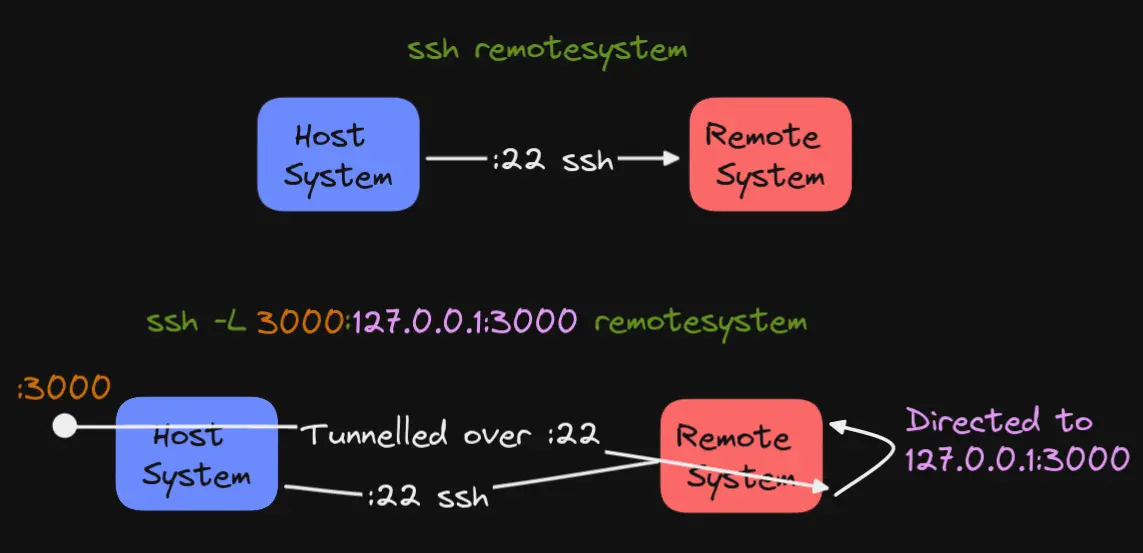
One major issue I have faced when working with remote servers is the firewall. Which is good! it means it's doing its job, as just having the IP of the device doesn't mean I should be able to access running services such as Grafana, Databases, etc.
ssh enables you to forward traffic from your system to the remote system over the "secure channel" on port :22
which is then directed to the port you specify from the remote system.
To do this you can use -L. For example, if I wanted to access port :3000 (typically Grafana) on the remote system I could use
ssh -L 3000:127.0.0.1:3000 remotesystem the format is port:host:hostport, it took me a little bit to understand how this comes
into play, hopefully a small diagram helps.
2a. Bonus! PortForward in your config.
I learnt while writing this that you can specify ports to forward for specific hosts in your ~/.ssh/config file! Wow, now I don't have
to disconnect and forward :3000 to see grafana each time.
# ~/.ssh/config
Host myserver
Hostname 192.168.1.10
User admin
LocalForward 3000 127.0.0.1:30003. Using git remotely via ssh
First things first, this functionality I used is considered a security issue. Please beware and understand the risk.
An issue I faced while configuring our AbandonTech server was pushing commits from a remote host after making changes. Our strategy was to maintain a git repository in the root folder of our deployment and then to keep it synchronized with a privately hosted git repository. This means duplication and/or recreation would be possible in dire situations.
I was able to author commits on the system, after configuring my git identity so I appeared as the correct user, but pushing those
authored commits was not going to be as simple. I could set up a rsync session to allow me to maintain a copy of the deployment
locally and on the server (including the .git folder). Which could lead me to overwrite changes created by other members of
the organisation on accident.
The simple solution for me was ForwardAgent. This is can be done by simply adding -A to your ssh connection, or adding it into your
~/.ssh/config.
# ~/.ssh/config
Host myserver
Hostname 192.168.1.10
User admin
ForwardAgent yesSo doing ssh -A abandontechserver allowed me to then git push to my heart's content. Do remember that -J or "Jump" is a safer
alternative, and I may update this article to explain it once I get to using it.
That's all folks
Well, that is it. A few incredibly useful features of ssh that "nobody told me about"... Well Google did, but I had to venture out on my own to find them. Hopefully it helps!
